Breaches and hacking attempts have become an almost daily occurrence at the moment.
This has been caused by the growth of IoT and cloud technology which has increased access to potential hackers.
Bad actors are making use of this new technology to damage your business or to steal from you.
Whether it’s your applications, infrastructure, or databases, IT professionals know how crucial it is to keep sensitive information safe.
The best way is to maintain a layer of protection between intruders and sensitive data.
According to CyberCrime Magazine,
60% of small companies go out of business within six months of falling victim to a data breach or cyber attack
What needs to be protected and monitored within an organization’s core systems?
- Network
- Web Applications
- Databases
- End Points
- Private and Public Cloud
What causes a website or web application to be hacked?
Being a developer myself, I have encountered several occasions when developers are given unreasonable deadlines to complete developing a web application.
Despite highlighting the potential problems especially those related to security, the project manager can only tell us to “Just Get it Done”!
The security loopholes that potentially could be overlooked include:
- SQL Injection – worst-case scenario causes the database to be accessible and editable by the intruder.
- Cross-Site Scripting – the behavior of the web application can be changed via Javascript being infused into pages.
- Password storage – critical to practice hashing calculation so it doesn’t appear obvious.
- Server-side request forgery – results in unauthorized actions or access to data through arbitrary command execution.
- Opened ports – Network ports that are unintentionally left open after some tests are completed.
As deadlines are met and workload eases, businesses must ensure to really look into the security aspects of their systems.
In this post, we will look at how businesses can benefit from utilizing a web app vulnerability scanning tool to counter the potential security loopholes mentioned above.
Recommended web app vulnerability scanning tool
When it comes to vulnerability assessments, the tool that comes to my mind has to be Tenable.
Tenable has security solutions for various industries ranging from automotive manufacturing to the oil & gas industry.
Tenable’s solutions are geared towards the following security requirements most businesses need:
- Application security
- Cloud security
- Compliance
- Ransomware deterrence
- Vulnerability assessment & management
- and more
One key product that will be covered in depth today is Nessus Professional – the vulnerability scanning tool your business needs.
Since I had an interest in securing web applications, I gave Nessus Professional a trial just to see how easy or difficult the tool is to use.
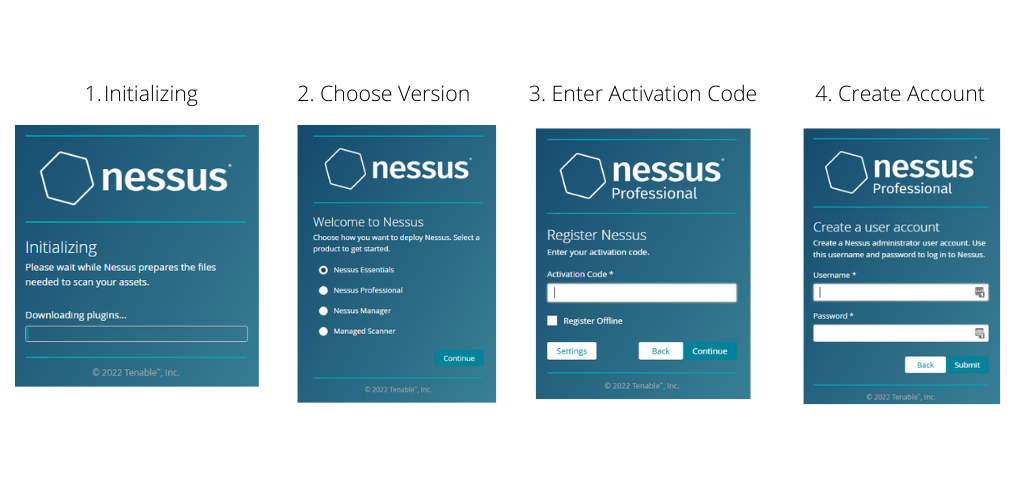
After downloading the Windows version, the application got installed within 30 minutes.
The first initializing step involves downloading the plugins required by Nessus to work.
The next step allows me to choose how I would like to deploy Nessus:
- Nessus Essentials
- Nessus Professional
- Nessus Manager
- Managed Scanner
Nessus Essentials is the “Home and Education use” version of the Nessus Pro product that has a limit of 16 IP addresses for vulnerability scans.
Nessus Pro allows unlimited IP addresses to be scanned with one license.
To fully discover what Nessus is capable of, I’ve proceeded to choose the Professional version which comes with a 7 days trial.
The next step would be to enter the activation code which is obtained when logged in to Tenable Community.
The last step would be to create a user account before it proceeds to complete the installation process.
Once the installation completes, a browser launches with a login page.
Upon signing in, I was quite impressed with the various types of vulnerability and compliance scans that Nessus Professional offers.
The various types of vulnerability scans include:
- Host Discovery – A simple scan to discover live hosts and open ports.
- Basic Network Scan – A full system scan suitable for any host.
- Advanced Scan– Configure a scan without using any recommendations.
- Advanced Dynamic Scan – Configure a dynamic plugin scan without recommendations.
- Malware Scan – Scan for malware on Windows and Unix systems.
- Mobile Device Scan – Assess mobile devices via Microsoft Exchange or an MDM.
- Web Application Tests – Scan for published and unknown web vulnerabilities using Nessus Scanner.
- Credentialed Patch Audit – Authenticate to hosts and enumerate missing updates.
- Intel AMT Security Bypass – Remote and local checks for CVE-2017-5689.
- Spectre and Meltdown – Remote and local checks for CVE-2017-5753, CVE-2017-5715, and CVE-2017-5754
- WannaCry Ransomware – Remote and local checks for MS17-010.
- Ripple20 Remote Scan – A remote scan to fingerprint hosts potentially running the Treck stack in the network.
- Zerologon Remote Scan – A remote scan to detect Microsoft Netlogon Elevation of Privilege (Zerologon).
- Solorigate – Remote and local checks to detect SolarWinds Solorigate vulnerabilities.
- ProxyLogon MS Exchange – Remote and local checks to detect Exchange vulnerabilities targeted by HAFNIUM.
- PrintNightmare – Local checks to detect the PrintNightmare Vulnerability in Windows Print Spooler.
- Active Directory Starter Scan – Look for misconfigurations in Active Directory.
- Log4Shell – Detection of Apache Log4j CVE-2021-44228
- Log4Shell Remote Checks – Detection of Apache Log4j CVE-2021-44228 via Remote Direct Checks
- Log4Shell Vulnerability Ecosystem – Detection of Log4Shell Vulnerabilities
- 2021 Threat Landscape Retrospective (TLR) – A scan to detect vulnerabilities featured in our End of Year report.
- CISA Alerts AA22-011A and AA22-047A – Detection of vulnerabilities from recent CISA alerts.
- ContiLeaks – Detection of vulnerabilities revealed in the ContiLeaks chats.
- Ransomware Ecosystem – Vulnerabilities used by ransomware groups and affiliates.
Although I was tempted to try out each vulnerability scan, I proceeded with the Web Application Testing scan to see what security issues might be discovered.
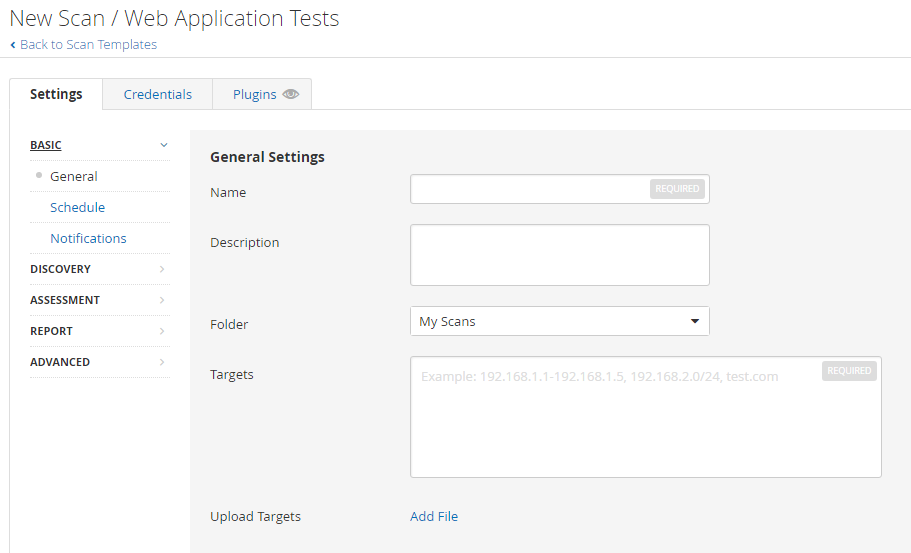
This is where a web application test scan can be defined and scheduled.
Although the scan and be executed manually, the ability to schedule a scan is a crucial feature to ensure that applications are constantly being monitored.
Most applications are developed by not just 1 developer but several developers.
Businesses cannot allow the mistake of a single developer to cause the system to be exposed thus the need for the scan to run on a schedule.
Email notifications can also be configured to send a report of the scanned results.
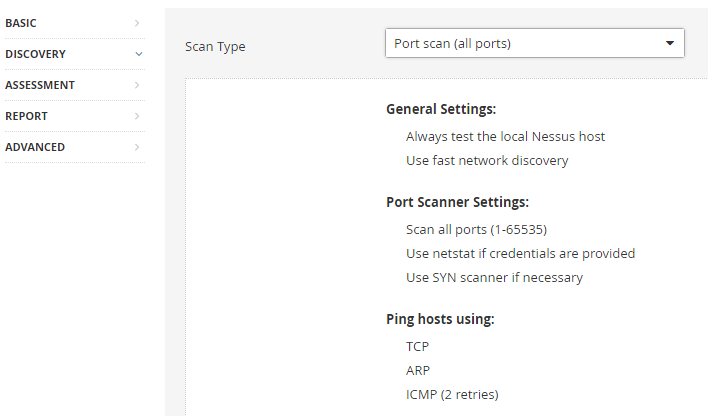
From the discovery section, the scan type allows for all ports or common ports to be scanned.
The custom scan type allows detailed discovery settings for more advanced users.
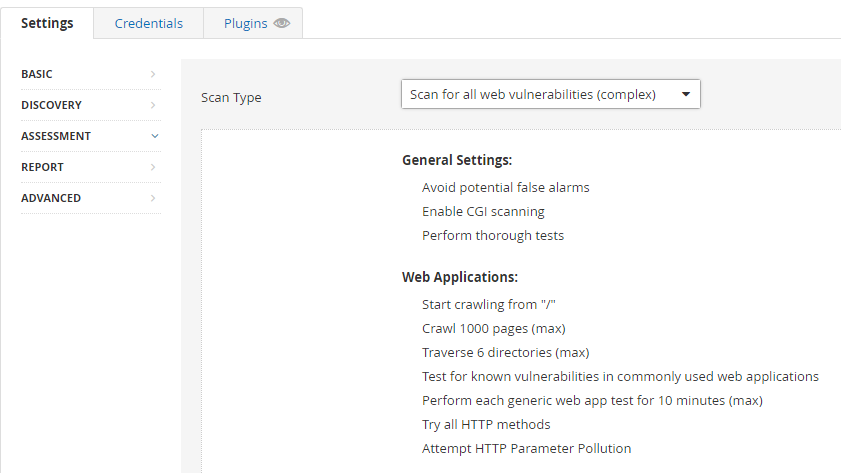
From the assessment section, I can choose to scan for known web vulnerabilities which include:
- CGI scanning
- Crawling into pages and directories
- Attempt HTTP Parameter Pollution – an exploit by injecting encoded query string delimiters in already existing parameters.
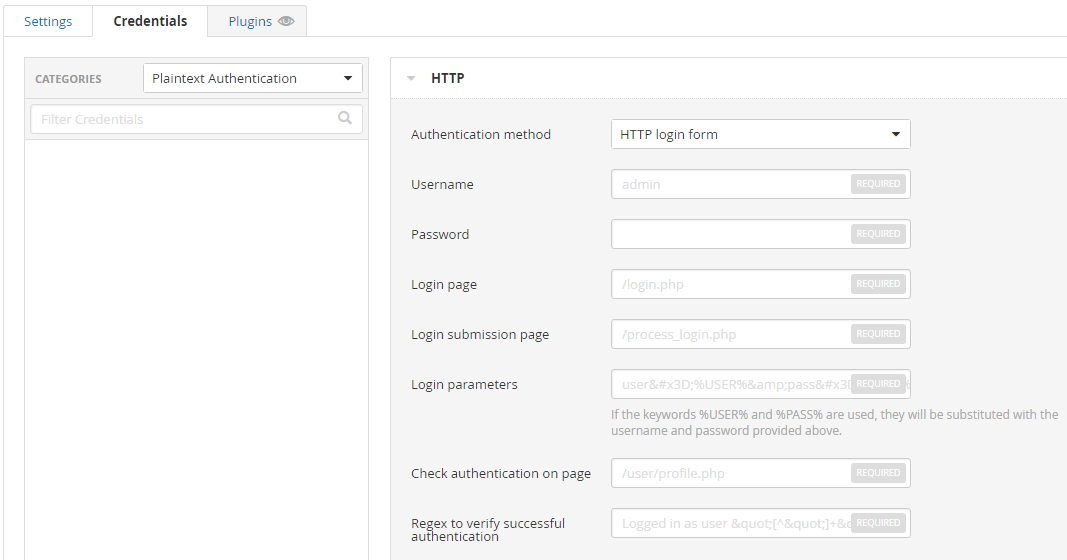
Most web applications’ landing page has a login form.
The credentials tab allows the username and password to be specified and checked against.
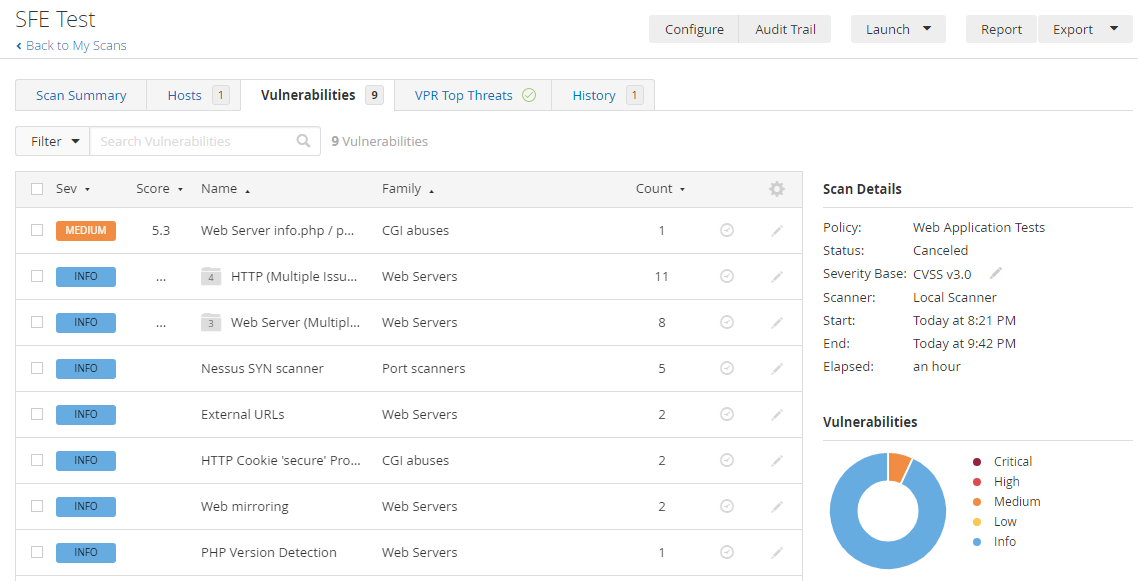
Since I got curious to find out if this site has any vulnerabilities, I ran a scan on it, and here are the findings.
I’m glad that Nessus found a vulnerability where I left a PHP file containing the output of phpinfo() in there.
Clicking on the Medium severity issue led to a page with the following information:
Many PHP installation tutorials instruct the user to create a PHP file that calls the PHP function ‘phpinfo()’ for debugging purposes. Various PHP applications may also include such a file. By accessing such a file, a remote attacker can discover a large amount of information about the remote web server, including :
- The username of the user who installed PHP and if they are a SUDO user.
- The IP address of the host.
- The version of the operating system.
- The web server version.
- The root directory of the web server.
- Configuration information about the remote PHP installation.Solution: Remove the affected file(s).
Without hesitating, I immediately FTP into my server to remove the file.
Photo by Klaus Nielsen
I’m glad to say that Nessus Professional does work very well and it’s worth the time to discover such a security tool all businesses need.
The benefits that this tool provides include:
- Accurate visibility into IT systems whether internal or on the cloud.
- Easy to deploy, implement, and maintain.
- Users get to benefit from Tenable’s Zero Day Research Team
- Advanced detection and cost-effectiveness for businesses of all sizes. (Hey, there’s even an Essentials version for Home and Education purposes.)
Look no further for other vulnerability scanning tools as your search should end with Tenable’s Nessus Professional.
Check it out today!










Leave a Comment