In today’s interconnected world, organizations increasingly rely on digital platforms and networks to conduct business.
To make sure their operations are safe from prying eyes, these businesses are forced to bolster their cybersecurity efforts.
One of the key components to building a comprehensive security strategy is to conduct regular security audits.
In this article, we will explore security audits and how Firewall Analyzer can simplify this critical process.
Understanding security audits
A security audit is the process of conducting a thorough examination of your organization’s network, policies, infrastructure and its effectiveness in combating threats and keeping your data safe and secure.
Security audits paint a clear picture of your network’s current standing in the face of an attack and help you identify vulnerabilities and areas of improvement.
With the rise in cybercrime, the number of attacks that companies and organizations have to fend off has increased. The average cost of a data breach in 2023 was $4.45 million, a 2.3% increase compared to 2022.
This underscores the importance of carrying out robust security audits, which can effectively help you protect your network from attackers.
Challenges in conducting a security audit
Security audits can be complex and challenging, depending on the organization and the scope of the audit. Here are the main hurdles associated with conducting a security audit.
- Defining the target: Establishing a clear scope is essential to ensure that the security audit covers the relevant sections of your organization’s landscape. This involves determining which networks, databases, apps, etc. need to be audited.
- Adapting to an evolving cyber landscape: Cybersecurity is an evolving space, and as an auditor, you need to keep up with the latest cybersecurity trends. This will enable you to safeguard your core business assets and protect them from attacks.
- Crafting clear reports: Security audit reports should contain clear and concise information about the cybersecurity issues present in your organization. Without an accurate report, it’ll be challenging for you to identify problems before they become critical and infect the system.
- Resource management challenges: The lack of skilled personnel can greatly impede security audits. Whether you have an in-house cybersecurity team that will carry out your security audits or are planning to outsource the security audit, it can be financially demanding.
- Human-factor challenges: Human error can impact the accuracy of the security audit. Miscommunication, insider threats, misinterpreting findings, and not following security procedures are a few examples.
The role of ManageEngine Firewall Analyzer
Conducting an effective security audit can be an intimidating task. However, with the right tools, like Firewall Analyzer and its robust set of features, it can be easy to streamline the entire audit process and transform it into a clean and actionable blueprint for strengthening your defense against cybersecurity incidents.
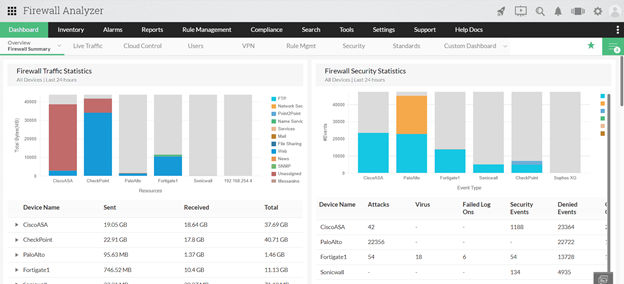
Figure 1. Firewall Analyzer’s Firewall Summary Dashboard
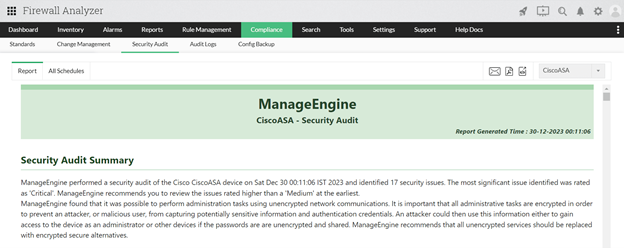
Figure 2. Firewall Analyzer’s Security Audit Summary
Performing a security audit with a firewall analyzer
ManageEngine Firewall Analyzer is a robust tool designed to simplify and enhance the security auditing process. It provides a comprehensive set of features for conducting security audits, including:
- Log analysis: ManageEngine Firewall Analyzer offers in-depth log analysis for firewalls, routers, IDSs, and IPSs to provide valuable insights into network traffic patterns, user behavior, and security incidents. Analyzing these logs is pivotal to identifying potential security risks or anomalies quickly.
- Compliance auditing: The tool offers out-of-the-box compliance reports for regulatory standards including the GDPR, SOX, HIPAA, etc. By running these reports, organizations can get updated information on the status of their alignment with industry-specific security requirements.
- Real-time alerts: Firewall Analyzer generates real-time alerts for security policy violations or security events. This allows organizations to respond to potential threats proactively. These alert notifications can be customized, ensuring timely action is enforced before threats blow out of proportion.
- Traffic analysis: Firewall Analyzer provides organizations with in-depth traffic usage, bandwidth consumption, application usage, and similar trend graphs. This invaluable information helps you optimize network performance, plan capacity, and identify potential security vulnerabilities.
- Historical and forensic analysis: This tool offers forensic analysis along with the option to store historic log data, which can be used to investigate security events. These features help pinpoint the root cause of an event, allowing you to implement preventive measures effectively.
- User activity monitoring: Firewall Analyzer helps keep tabs on user activity. With this tool, you can monitor user activities, and web application usage, track login and logout times even via VPN, detect unusual behavior, and deter unauthorized behavior.
In today’s threat-ridden security environment, investing in a tool like Firewall Analyzer is no longer a recommendation but a necessity.
Conduct regular security audits, identify vulnerabilities, strengthen your defenses, and maintain a strong network security posture for your organization with Firewall Analyzer.
Interested? Sign up for a personalized demo, get our best price, or download Firewall Analyzer today for a free, 30-day trial.



Leave a Comment